Table of contents
What is tokenization?Credit card tokenization historyTokenization vs. encryptionTokenization examplesFAQs about tokenization
“Tokenization” is a super-buzzy payments word at the moment, especially because of the increased attention on mobile payments apps like Apple Pay. Basically, tokenization adds an extra level of security to sensitive credit card data.
What is tokenization?
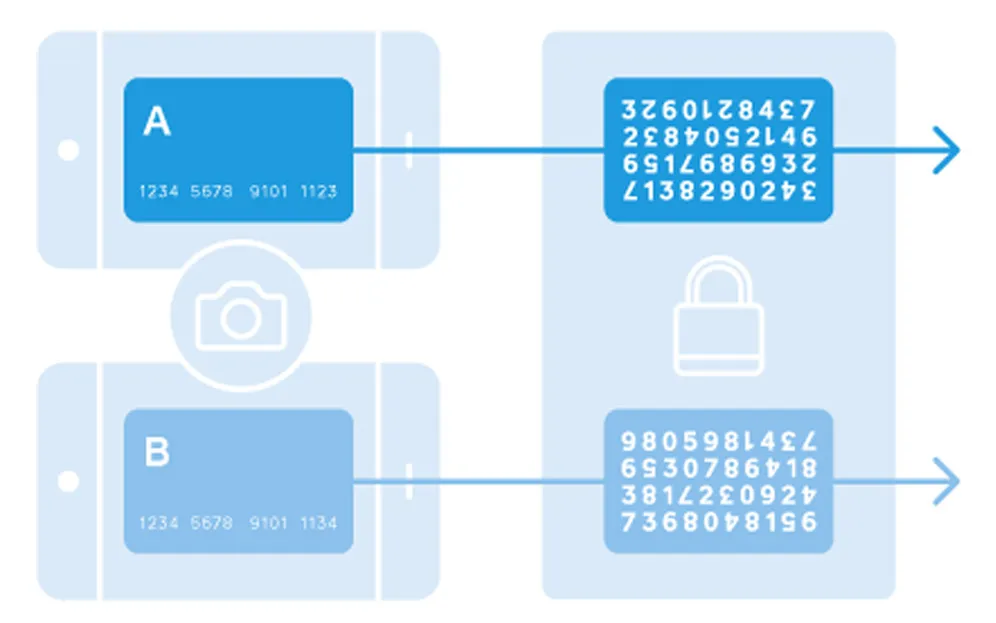
Tokenization is the process of protecting sensitive data by replacing it with an algorithmically generated number called a token. Often times tokenization is used to prevent credit card fraud. In credit card tokenization, the customer’s primary account number (PAN) is replaced with a series of randomly-generated numbers, which is called the “token.” These tokens can then been passed through the internet or the various wireless networks needed to process the payment without actual bank details being exposed. The actual bank account number is held safe in a secure token vault.
Just like the nationwide shift to chip cards, tokenization’s end game is to prevent the bad guys from duplicating your bank information onto another card. But while chip cards protect against fraud that occurs when someone pays at a physical store, tokenization is primarily designed to fight online or digital breaches.
Learn more -/^Bring together your checking, savings, and loans
Credit card tokenization history
Substitution techniques like tokenization have been in practice for decades as a way to isolate data in ecosystems like databases. Historically encryption with reversible cryptographic ‘keys’ was the preferred method of protecting sensitive data. According to Stanford University’s encryption expert, “Encryption is the transformation of data into a form unreadable by anyone without a secret decryption key. Its purpose is to ensure privacy by keeping the information hidden from anyone for whom it is not intended, even those who can see the encrypted data. For example, one may wish to encrypt files on a hard disk to prevent an intruder from reading them.” Encryption has a wide variety of use cases, from cloaking private messages in P2P apps to transferring sensitive information in a vulnerable environment.
But more recently, payment experts are seeing more and more organizations moving from encryption to tokenization as a more cost-effective (and secure) way to protect and safeguard sensitive information.
One of the most widespread uses of tokenization today is in the payments processing industry. Tokenization allows users to store credit card information in mobile wallets, ecommerce solutions and POS software to allow the card to be recharged without exposing the original card information.
Tokenization vs. encryption
| Criteria | Tokenization | Encryption |
| PAN data displayed | X | |
| Mathematically reversible | X | |
| Reduces PCI scope | X | |
| Payment flexibility: refunds, chargebacks, recurring payments etc. | x | |
| Rotation of keys required | X | |
| End-to-end security | X | |
| Low-cost per transaction | X | |
| Format fits with legacy credit card fields | X | |
| Centrally managed | X | |
| Established security | X |
Tokenization replaces sensitive cardholder detail with a stand-in token. This helps secure the customer’s bank account details in credit card and eCommerce transactions.
End to end encryption (aka “data field encryption”) on the other hand, encrypts cardholder data at the origin, and then decrypts it at the end destination. Some examples of end-to-end encryption are VPNs, Apple’s imessage feature, and other messaging apps like WhatsApp.
Both tokenization and encryption are used to reduce the scope of PCI Compliance by reducing the amount of systems that have access to customers’ credit card information. (For a primer on PCI compliance, check out our PCI Compliance Guide). While both have their places in payment technology, tokenization is fast emerging as a more cost-effective and secure solution to protecting customer card information and reducing the scope of PCI compliance. Unlike data that is encrypted, tokens are not mathematically reversible with a decryption key and PAN data is never displayed.
Tokenization examples
How is tokenization put to use in the payments industry? Three ways. The first is when businesses keep your “card on file” for subscription billing and recurring payments. The second is on eCommerce sites that offer frequent, returning customers “one-click” checkouts. And the third use (and perhaps the buzziest, as of late) is within NFC mobile wallets like Apple Pay and Android Pay.
Payment tokenization: An explainer
Here’s how tokenization helps protect you in the following payment scenarios:
Apple Pay tokenization. After you take a picture of your credit card and load it into your iPhone 6, Apple sends the details to the card’s issuing bank or network, which replaces your card details with a series of randomly generated numbers (the token). That random number is sent back to Apple, which programs it into the phone. This means that the number stored on the phone can’t be extracted into anything valuable to fraudsters.
Android Pay tokenization. Tokenization in Android Pay works similarly. When you upload your card information into the app, Google creates a stand-in “token,” to represent your actual account number. This makes it near impossible for someone to get at your actual credit card information.
Tokenization within apps. Say you want to buy something straight from an app on your phone — concert tickets, clothes, books, whatever. If your phone contains a token, none of these apps have access to your credit card details. Read: Your bank information is locked down and meaningless to fraudsters. Using a tokenized account also can make it easier to check out, as many apps will link directly to your stored shipping information.
Tokenization in eCommerce. Tokenization also helps protect your online shopping activities. You buy a coffee table on Ikea.com, for example. If IKEA has tokenized the card numbers that it keeps on file, your information is safe even if it gets hacked (which it hasn’t). The retailer may never actually see or store the credit card number, so if someone weasels into the system (like in the Home Depot breach, for example), all the criminal can see is the randomly generated tokens. And here’s something else that’s cool: A new token can be generated for each online retailer — so you’ll have a different code at all the places you’ve shopped. So if a retailer has a security breach, all tokens issued to that website can be disabled without you having to get a replacement card.
In short: Tokenization is a complicated topic, but it’s good to know the basics (and if you’re more visually inclined, we made a simple graphic illustrating how it works above). It’s an exciting evolution in keeping every kind of payment more secure.
FAQs about tokenization
Is tokenized data reversible?
Tokenized data is not mathematically reversible unless you have the original key used to create the token.
How are tokens generated?
Tokens can be generated through mathematically reversible algorithms, one-way non-reversible cryptographic functions, or static tables mapped to randomly generated token values
Does using tokenization make me PCI compliant?
Employing tokenization won’t in and of itself make you PCI compliant, but it’s considered a “best practice” and can help to reduce PCI DSS scope. You can see the PCI Security Standards Council best practices on choosing tokenization providers here. But not to worry, Square provides an affordable, PCI-compliant solution.
Learn more about how payment processing fees work with Square.
![]()